
Полезное:
Как сделать разговор полезным и приятным
Как сделать объемную звезду своими руками
Как сделать то, что делать не хочется?
Как сделать погремушку
Как сделать так чтобы женщины сами знакомились с вами
Как сделать идею коммерческой
Как сделать хорошую растяжку ног?
Как сделать наш разум здоровым?
Как сделать, чтобы люди обманывали меньше
Вопрос 4. Как сделать так, чтобы вас уважали и ценили?
Как сделать лучше себе и другим людям
Как сделать свидание интересным?

Категории:
АрхитектураАстрономияБиологияГеографияГеологияИнформатикаИскусствоИсторияКулинарияКультураМаркетингМатематикаМедицинаМенеджментОхрана трудаПравоПроизводствоПсихологияРелигияСоциологияСпортТехникаФизикаФилософияХимияЭкологияЭкономикаЭлектроника

To guard against brute-force attacks, the key needs to be sufficiently long
|
|
To reduce the memory access time which of the following internal memory is used? =Cache
To resolve the clash over the access of the system BUS we use __________.=Bus arbitrator
To which of the following possible type of operations do the following view depict? =Data movement
To which of the following possible type of operations do the following view depict? =Data storage
To which of the following possible type of operations do the following view depict? =Processing from/to storage
To which of the following possible type of operations do the following view depict? =Processing from storage to I/O
Traditional First-In First-Out (FIFO) packet schedulers are insufficient for offering Quality of Service (QoS) guarantees in an integrated services network because the schedulers typically (d) treat all packets with the same priority 100%
Triggering phase: The virus is activated to perform the function for which it was intended. As with the dormant phase, the triggering phase can be caused by a variety of system events, including a count of the number of times that this copy of the virus has made copies of
Types of Information Systems: a. Informal Information System d. Formal Information System
Typically, a network protocol specifies which of the following? (d) I and II 100%
Use case diagram "Hairdressing salon" has 2 actors: client & haircutter and 4 use cases: "make apoinment", "wash head", ""take haircut" and ""pay". Some use cases are extend or include and others just use cases. What combination of use cases is right for Use case diagram "Hairdressing salon"? e. make & take are just, wash is extend to take, pay is include to take
User Datagram Protocol (UDP) uses which of the following for optional error detection? (d) One's complement sum 100%
Using a ______ you can do exchange the data between the different applications and different platforms. c. Web services;
Usual transistor functions as a high-speed binary switch and implements the logic function: 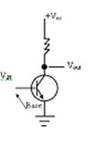 =Logical negation#
=Logical negation#
Vendors release small pieces of software to repair flaws. However exploits often created faster than patches be released and implemented b. True
Vernam cipher is also called as a _____________. One time pad
Web Services define a platform-independent standard based on XML to communicate within distributed systems.. b. True
Web Services. The UDDI is: b. Universal Description, Discovery and the Integration Service;
Web Services. The WSDL is: d. Web Services Definition Language;
Web Services. UDDI is used for listing what ______ are available. a. services;
Web Services. What is SOAP: d. Simple Object Access Protocol
What actions does not belong to Security policy d. Install several antivirus programs
What activate the decoder by the value their n-inputs? =One of their outputs#
What algorithm fills the shape using the point? = 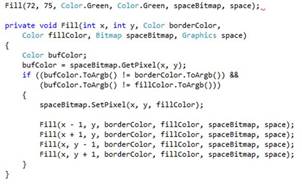
What are common techniques used to protect a password file? One way encryption, Access control.
What are some approaches to producing message authentication? Message encryption, Message authentication code and hash
What Are Strings? are a sequence of characters
What are the essential ingredients of a symmetric cipher? I. Plaintext II. Secret key II. Encryption algorithm IV. Decryption algorithm
What are the parts required to build a standard RS-trigger chip (asynchronous RS-trigger) using the bipolar transistors and NOR schemes?=Four transistors
What are the two basic functions used in encryption algorithms? Permutation, Substitution
What are the two general approaches to attacking a cipher? Brute force, Cryptanalysis
What can a pointer store? All of the statements Or ( pointer to function taking a char* argument and returns an int )
What can't harm an information system? c. Tokens
What did the least complicated among the revised adder chips for the two same-order addition contain? =Three transistors
What does Antivirus and antispyware software? c. Checks computers for presence of malware and can often eliminate it as well
What does enable hackers to steal proprietary information such as e-mail, company files, etc.? d. Sniffer
What does escape sequence \" do? Used to print a double quote character
What does escape sequence \a do? Sound the symbol bell
What does escape sequence \n do? Position the screen cursor to the beginning of the next line
What does escape sequence \r do? Position the screen cursor to the beginning of the current line; do not advance to the next line
What does escape sequence \t do? Move the screen cursor to the next tab stop
What does Identity management software? c. Authenticates users, protecting identities, controlling access
What does Intrusion detection systems? d. Examines events as they are happening to discover attacks in progress
What does not belong to Authentication? b. Encryption
What does not belong to Digital certificate? b. Use of public key cryptography working with certificate authority
What does not belong to Ensuring software quality? c. Software classification
What does the Capacity characteristic of memory define? =Defines number of words for internal memory and number of bytes for external memory.
What does the difference's order of the output always match for the single-order adder-subtractor chip performing both adding and subtraction?=Addition result of two same orders
What does the following SQL statement do: SELECT Customer, COUNT(Order) FROM Sales GROUP BY Customer HAVING COUNT(Order) >5 d. Selects all customers from table Sales that have made more than 5 orders.
What does the following statement mean? pointer to function taking a char* argument and returns an int
What does the Location characteristic of memory define? =Refers to whether memory is internal and external to the computer.
What does the PC's TLB buffer contain? =Recently accessed virtual tables' ids
What does the RAID stands for?=Redundant Array of Independent Disks
What does the simplest RS-trigger scheme contain? =Two complementary outputs, one of which is main
What does the TLB buffer allow? =Faster conversion from virtual to physical addresses
What does the unary scope resolution operator (::) do? Access global variable if local variable has same name
What does the Unit of transfer characteristic of memory define? =Defines the number of electrical lines into and out of the memory module.
What does this instruction mean? <xsl:apply-templates select="//div" /> c. This means "Find all the elements in the document, and process them according to any applicable templates".
What does this XSLT output: <xsl:text disable-output-escaping="yes"> <!-- hello --> </xsl:text> b. It will not output anything
What does use of numerous computers to launch a DoS? b. Distributed denial-of-service attacks
What happens when a class with parameterized constructors and having no default constructor is used in a program and we create an object that needs a zero-argument constructor? Compile-time error
What has become more important because of the increased use of computers, the internet and WWW. Data integrity, data security
What have caused the rise in computer crimes and new methods of committing old computer crimes? Increase using computer extension
What is a Denial of Service? Preventing
What is a difference between a declaration and a definition of a variable? A declaration occurs once, but a definition may occur many times
What is a fractal? =A fractal is a mathematical set that has a fractal dimension that usually exceeds its topological dimension and may fall between the integers. And a parent element is similar to a child.
What is a Masquerade? One entity pretends to be a different entity
What is a Modification of messages? Altering. What is a Replay? The passive
What is a salt in the context of UNIX password management? Is combined with password
What is argument coercion? Force arguments to be of proper type
What is Difference Between UNION and UNION ALL? e. UNION combine all row of both table, while UNION ALL select only atomic rows of both table
What is ER Model? ER model.. b. is a way of graphically representing the logical relationships of entities (or objects) in order to create a database
What is Pseudocode? an artificial and informal language that helps programmers develop algorithms without having to worry about the strict details of C++ language syntax
What is redirecting Web link to address different from intended one, with site masquerading as intended destination? c. Spoofing
What is Relational Model disadvantage? b. hardware overheads
What is result of Global Integration? If a.R1(prof, course, university) and b.R2(title, prof, course) a. Global(prof,course,title,university)
What is right for "cookie"? a. a small piece of text containing identifying information e. can be stored permanently or for a limited time
What is right for Actor? a. Someone or something that interacts with the system d. Typically, an actor represents a role that a human, a hardware device, or even another system plays with a system
What is right for Disaster recovery and Business continuity planning? a. All are right
What is right for Random File Organization? b. Organization may be Direct/Indexed e. Go directly to desired record by using a key
What is right for Sequential File Organization? a. Records are stored in the order they were entered c. Tape storage uses sequential organization d. If a particular record is desired, all prior records must be read first What is right for Use case model? a. Illustrate a system b. Use cases are usually described in a textual document that accompanies a use case diagram; the combination of these use case diagrams & their supporting documentation is known as a use case model d. Are used to communicate
What is the block length in DES? 64-bit
What is the cause for the necessity for introduction of the cache chip into the CPU <->Main memory interaction system?=Big memory access time compared to the CPU's operation time.
What is the child element (motif) of the Koch Curve? = 
What is the child element (motif) of the Koch Island? = 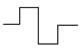
What is the child element (motif) of the Koch Snowflake? = 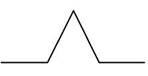
What is the difference between Data Integrity and Data Security? Consistent accurate and reliable data, potential data from unauthorized access
What is the difference between the WHERE and HAVING SQL clauses? d. The WHERE SQL clause condition(s) is applied to all rows in the result set before the HAVING clause is applied (if present). e. The HAVING clause is used with SELECT SQL statements and specifies a search condition for an aggregate or a group.???
What is the File Management System? c. Volkov Commander
What is the formula for defining a Z-multiplexor (see pic.) 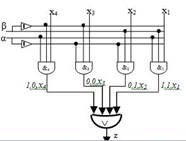 with two operation outputs α,βand appropriate x1, x2, x3, x4 data inputs? =
with two operation outputs α,βand appropriate x1, x2, x3, x4 data inputs? = 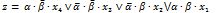
What is the functionality of a block-cipher? Processes the input one block of elements at a time
What is the functionality of a stream-cipher? Processes the input elements ]What is the key length in DES? 56-bit
What is the input combination J = 1, K = 1 for the JK-trigger chip? =It is always allowable
What is the input ports' combination R = 1, S = 1 for the RS-trigger chip? =The combination is always illegal
What is the Koch Curve? = 
What is the Koch Island? = 
What is the Koch Snowflake?= 
What is the non-system vulnerability? b. Theft of portable devices
What is the non-system vulnerability? c. Theft of portable devices
What is the output of the code below? good satisfactory
What is the output of the code below? Not a Not b
What is the output of the single-order ALU for the fixed set of α, β=Result of the one operation
What is the output of this program? it will return memory address of integer b
What is the output of this program? ABCDEFGHIJ
What is the output of this program? fg
What is the output? 1 2 3 4
What is the purpose of Active Attack? To alter …. What is the purpose of Passive Attack? To learn …
What is the purpose of the S-boxes in DES? function that integrates
What is the result of the input combination J = 1, K = 1 for the JK-trigger chip? =Inverted value of the previous trigger's output#
What is the role of the Direct Memory Access (DMA)? =The DMA controls the exchange of data between main memory and an I/O module.
What is the role of the I/O address register (I/OAR) in the CPU? =specifies a particular I/O device.
What is the role of the I/O buffer register (I/OBR) in the CPU? =is used for the exchange of data between an I/O module and the CPU
What is the role of the Interrupt-driven I/O? =With the Interrupt-driven I/O, the CPU issues an I/O command, continues to execute other instructions, and is interrupted by I/O module when the latter has completed work.
What is the role of the memory address register (MAR) in the CPU? =specifies the address in memory for the next read or write
What is the role of the memory buffer register (MBR) in the CPU? =contains the data to be written into memory or receives the data read from memory
What is the role of the Programmed I/O? =With the Programmed I/O data is exchanged between the CPU and I/O module.=With the Programmed I/O, the CPU issues an I/O command, continues to execute other instructions, and is interrupted by I/O module when the latter has completed work.
What is the size of an array according to the code above? 6
What isn't right for Indexed File Organization? e. Go directly to desired record by using a key
What isn't right for Manual Global Integration? a. Automaticaly merge multiple databases into a new global database
What isn't right for MIS audit? a. Lists and ranks all program protocols
What isn't right for Public key encryption? a. Sender and receiver use single, shared key
What number will z in the sample code below contain? 10 (ne tochno)
What output set does the decoder activate according to the value of its n inputs? =one-unit, all remaining zeros set
What primitive operations are used in RC4? XOR, key swap
What substitution system results when we use a 25 x 1 Playfair matrix? Mixed Caesar cipher
What technologies does not include Firewall? b. Authenticates users, protecting identities, controlling access
What value will x contain when the sample code below is executed? 2
What will be output of the following code if 32 is inputted when program run? Even
What will be output of the following code if 7 is inputted when program run?} odd
What will be printed when the sample code above is executed?; 5
What will be printed when the sample code above is executed? 56789 0123456789
What will be the output of the code below if we inputted 'm' when program run?} Male emale
What will be the output of the code below: 0 -1 0
What will be the output of the code below: 307
What will be the output of the code below: 357
What will be the output of the code below: 427
What will be the output of the code below: 2 1 2
What will be the output of the code below? 21
What will be the output of the following code? 54
What will be the output of the following program if we inputted 84 when program run? Compilation error
What will be the output of the following program? 0
What will be the output of the following program? 15
What will be the output of the following program? 2
What will be the output of the following program? -1
What will be the output of the following program? 15 15 30 30
What will be the output of the following program? Char
What will be the output of the following program? 10 40
What will be the output of the following program? a = 20 b = 30
What will be the output of the program? 103.Net
What will be the output of the program? Equal (но пишет что правильный Unequal TAK NAPISANO V DOC “ALG FULL”)
What will be the output of the program? Evening!
What will be the output of the program? Hello World
What will be the output of the program? kk
What will be the output of the program? 100 200
What will be the output of the program? 25 4
What will be the output of the program? 6 6
What will be the output of the program? BC
What will be the output of the program? x and y are equal
What will be the output of the program? #3
What will be the output of the sample code above? 5
What will be the output? 3
What will be the output? 4 8
What will be the output? Hello
What will be the output? 1
What will be the output? 100
What will be the output? 2
What will be the output? 21 31
What will be the output? 237
What will be the output? 4
What will be the output? 9
What will be the output?(string) Hello World
What will be the output? 0
What will be the output?4
What will be the output? Hello Hi
What will be the result of the code fragment: double number = 12.5; std::cout << "The result of is " << number%5; Compilation error.
What will be the result of the following SQL statement: SELECT * FROM Table1 HAVING Column1 > 10 d. The SQL statement will generate an error.
What will be the result of the following statement? SELECT 100 + NULL b. NULL
What will be the result of this SQL query: SELECT pname FROM product WHERE pname LIKE ‘_k%’;. a. pNames containing "k" as second char
What will be the value of c after the execution of portion of code below: 4
What will be the value of c after the execution of the following statement: 7
What will be the value of product after the execution of portion of code below0
What will be the value of product after the execution of portion of code below: 120
What will be the value of x after the execution of the statement below: int x = 7 % 13 + 2 * 2 - 2 / 2; 10
What will be the value of x after the execution of the statement below: int x = 7 + 3 * 5 / 2 - 1; 13
What will be value of x and y after the execution of the code below: int x=10, y=15; x = x++; y = ++y; 10 16
What will happen in this code?; p now points to b
What will happen when the program above is compiled and executed? There is no output, because It causes infinite loop
What will print when the sample code above is executed? 1
What will the code above print when executed? -3: 4 -4: 3
What's the role of Arithmetic and logic unit (ALU) in computer? =Performs the computer’s data processing functions
What's the role of Control unit in computer? =Controls the operation of the CPU and hence the computer
What's the role of CPU interconnection in computer? =Provides for communication among the control unit, ALU, and registers
What's the role of I/O in computer? =Moves data between the computer and its external environment
What's the role of Main memory in computer? =Stores data
What's the role of Registers in computer? =Provides storage internal to the CPU
What's the role of System interconnection in computer? =Provides for communication among CPU, main memory, and I/O
When a member function is defined outside the class definition, the function header must include the class name and the _________, followed by the function name to "tie" the member function to the class definition.::
When an argument is _______________, a copy of the argument's value is made and passed (on the function call stack) to the called function. Changes to the copy do not affect the original variable's value in the caller. passed by value
When applied to a variable, what does the unary "&" operator yield? The variable's address
When creating a DTD for an existing XML document, when should you determine the root element? Please select all the correct answers. a. Before you determine the document tree structure for the elements b. As the first step
When performing algebraic operations "addition" and "subtraction" of the floating-point numbers is required to determine what the internal operation is required to perform effectively over the mantissa m1 and m2. If the numbers have different signs, and the external operation is subtraction, the internal operation of the mantissa=addition
When performing algebraic operations "addition" and "subtraction" of the floating-point numbers is required to determine what the internal operation is required to perform effectively over the mantissa m1 and m2. If the numbers have same signs, and external operations on numbers is subtraction, than the internal operation on the mantissa=subtraction
When performing algebraic operations "addition" and "subtraction" of the floating-point numbers is required to determine what the internal operation is required to perform effectively over the mantissa m1 and m2. If the numbers have different signs, and external operations on numbers is addition, than the internal operation on the mantissa{ =subtraction
When performing algebraic operations "addition" and "subtraction" of the floating-point numbers is required to determine what the internal operation is required, in fact performed on the mantissa M1 and M2. If the numbers have the same sign, and the addition of a foreign operation, the internal operation{ =addition
When performing arithmetic operations on two machines (normalized) numbers with the internal operation of subtraction, if the alignment order is not happening, then you can immediately implement the subtraction in column major negative consequence of such a deduction is=Loss of the normalization of the result and the need to normalize the "left" with a simultaneous decrease in the number of adder-order equal to the number of digits, which is a shift
When the same DTD declaration is found in the internal and external subset, which one has priority? The one from the external subset or the one from the internal subset? b. internal subset
When we mention the prototype of a function? Declaring
When you perform an operation (addition, subtraction) of two machine numbers in the lower order leveling orders increased to a greater number of the mantissa, and a smaller order{=Shifts to the right in the register by the number of bits equal to difference of orders
When you perform an operation (addition, subtraction) of two machine numbers, after cleaning and loading the operand registers for operands and registers its internal operations, the control unit determines the difference p1-p2 - order operands. If p1-p2\= 0 then "stacked" the corresponding operation is performed on the mantissa, otherwise, if p1!\= p2, then before the addition of the mantissas is required to make{=alignment operation orders, increasing the smaller of them till bigger
Where is the PC's virtual memory situated? =in the operating system layer
Where the default value of parameter have to be specified? Function prototype
Which access method enables to make a comparison of desired bit locations within a word for a specified match, and to do this for all words simultaneously? =Associative=Sequential
Which bus buffers data circulating between the Main Memory and peripheral devices’ controllers allows to support a large variety of external devices? =Expansion Bus
Which bus type assigned to a single function (e.g. address bus) or a physical subset of components (e.g. I/O bus connects all I/O modules). =Dedicated
Which bus type can be used for both addresses and data. In this case, an address valid control line is needed to determine whether the data is an address or data. =Multiplexed
Which bus unites high-speed external devices and is connected with the System Bus through special concordance module - Bridge. =High-Speed Bus
Which cipher is based on the use of a 5 пїј 5 matrix of letters constructed using a keyword. Plaintext is encrypted two letters at a time using this matrix. Playfair
Which classical cipher involves replacing each letter of the alphabet with the letter standing k places further down the alphabet, for k in the range 1 through 25. Caesar triction cipher
Which clause specifies conditions that determines the groups included in the query? c. having
Which clause you can use to restrict groups returned by a grouped query. d. HAVING
Which component controls the operation of the computer and performs its data processing functions? =Central Processing Unit (CPU)
Which component Moves data between the computer and its external environment? =I/O devices
Which computer was designed and constructed at the University of Pennsylvania, was the world’s first general- purpose electronic digital computer. =ENIAC
Which is definition of Information System wrong? e. IS is the tool used to store, manipulate, distribute or create The method of joining two tables together in SQL is: c. Join
Which is the correct way to use the union operator: d. <xsl:apply-templates select='/CD/Artist | /Tape/Artist' />
Which key is a temporary encryption key used between two principals. Session key
Which malicious program attaches itself to a program and propagates copies of itself to other programs? Virus
Which malicious program Captures keystrokes on a compromised system? Keylogger
Which malicious program embedded in a computer program that checks for a certain set of conditions to be present on the system. When these conditions are met, it executes some function resulting in unauthorized actions? Logic Bomb
Which malicious program is activated on an infected machine to launch attacks on other machines? Zombie
Which malicious program is used to send large volumes of unwanted e-mail? Spammer ]Which malicious program propagates copies of itself to other computers? Worm
Which malicious program that allows unauthorized access to functionality of the system? Backdoor (Trapdoor)
Which malicious software is used to cause DoS (Denial of Service) attack against particular web site? Worm
Which memory device is generally made of semi-conductors? =RAM
Which memory device is NOT generally made of semi-conductors? =CD
Which of one of the following is NOT TRUE? =Multiple devices at a time can successfully transmit.
Which of the following access specifier is used as a default in a class definition? private
Which of the following access specifies is used in a class definition by default? private
Which of the following allows a host to be assigned an IP address automatically (d) The dynamic host configuration protocol (DHCP) 100%
Which of the following also known as an instance of a class? Object
Which of the following approximates a global physical clock that uses the happens-before partial order? (d) Logical clock 100%
Which of the following are basic security functions of the firewall? Packet filtering, Application proxy gateways
Which of the following are drawback of using Personal/Small Business Firewalls? Some firewalls don’t do outbound connection blocking, Some firewalls are inconvenient to configure, Most guard only against IP threats
Which of the following are examples of the host dependent malicious programs? Logic Bombs, Trap door
Which of the following are examples of the host independent malicious programs? Zombie, Which of the following are the solutions to network security?, II, III and IV
Which of the following are not a group function? a. sqrtegg (sqrt()) e. round()
Which of the following are valid XML names? (check all valid options) b. Size- c. data-xml
Which of the following below are features of firewall? I, II and III
Which of the following below are features of firewall? I, II and III
Which of the following below is not a component of the computer? =External memory
Which of the following below is not a component of the CPU? =Main memory
Which of the following can access private data members or member functions of a class? Any member function of that class.
Which of the following can be overloaded? Both functions and operators
Which of the following can be used by a router to report a dropped packet to the packet's sender? (d) Internet Control Message Protocol (ICMP) 100%
Which of the following can be used for user authentication? I.Kerberos II.Secure Socket Layer (SSL) (d) I and II 100%
Which of the following concept of OOP(Object-oriented programming) allows compiler to insert arguments in a function call if it is not specified? Default arguments
Which of the following concepts provides facility of using object of one class inside another class? Composition
Which of the following cryptosystems, if implemented properly, is impenetrable? One time pad
Which of the following declarations must every XML document that uses a DTD have? Please select the best answer. d. A <!DOCTYPE> declaration
Which of the following distributed-computing frameworks represents client-server interactions as simple function invocations? (d) Remote Procedure Call (RPC) 100%
Which of the following does not use a hierarchical naming convention? (d) Service Location Protocol (SLP) 100%
Which of the following features of Ethernet has not remained constant since the advent of the technology? (d) Transmission bandwidth 100%
Which of the following functions are performed by a constructor? Initialize objects
Which of the following internet applications typically transmit(s) packets over Transmission Control Protocol (TCP)? I.FTP client II. Audio streaming III. Web browser (d) I and III only 100%
Which of the following IP header fields is designed to prevent a packet from remaining indefinitely in a routing loop? (d) Time to live 100%
Which of the following IP header fields provide simple error detection? (d) Checksum 100%
Which of the following is (are) component(s) of Control Unit?=I, II and III
Which of the following is (are) concept(s) of Hardwired Program?=I, II and III
Which of the following is (are) true about distributed file systems? I.Files and directories are stored on network servers. II.Distributed file systems typically support fine-grained sharing. III.Distributed file systems typically use communicating protocols such as Remote Procedure Call (RPC). (d) I and III only 100%
Which of the following is (are) true about Quality of Service (QoS) networks? I.The complexity of routers is less than in other kinds of networks. II.Routers must maintain more state information than in other kinds of networks. (d) II only 100%
Which of the following is (are) true of local area wireless networks? I.They are typically based on cells using point-to-point media links. II.Two wireless hosts can be within transmission range of the base station but out of range of each other. III.They have higher roundtrip delays than similar wired networks. (d) II only 100%
Which of the following is (are) used by distributed computer systems to synchronize clocks? I.Network Time Protocol (NTP) II.Global Positioning System (GPS) (d) I and II 100%
Which of the following is (are) weakness(es) of Caesar cipher? I, II and III
Which of the following is / are the types of firewall? All of the statments
Which of the following is a disadvantage of connection-based protocols? (d) High startup costs 100%
Which of the following is a protocol used for communication between a web server and a web browser? (d) HTTP 100%
Which of the following is a standard that a network program can use to specify the type of a transmitted document? (d) Multipurpose Internet Mail Extensions (MIME) 100%
Which of the following is an advantage of using Personal/Small Business Firewalls? Some let you
Which of the following is an example of the host dependent malicious programs? Virus
Which of the following is considered a good choice for a password? None of the statements
Which of the following is correct about function overloading? I. The types of arguments are different. II. The order of argument is different
Which of the following is illegal? int i; double* dp = &i;
Which of the following is not the member of class? friend functions
Which of the following is NOT the operation that CPU performs? =Data transfer
Which of the following is NOT TRUE regarding to Secure Socket Layer (SSL)? Takes place at the network layer
Which of the following is offered by both Serial Line IP (SLIP) and Point-to-Point Protocol (PPP)? (d) Flow control 100%
Which of the following is responsible for providing a safe running environment for Java applets? (d) The Web browser 100%
Which of the following is the correct way of declaring a function as constant? III. int ShowData(void) const { /* statements */ }
Which of the following is the network-layer protocol of the Internet? (d) IP 100%
Which of the following is the only technical difference between structures and classes in C++? Member function and data are by default public in structures but private in classes.
Which of the following is true about Object Resource Brokers (ORBs) that are implemented by different vendors? (d) All vendors are free to choose their own implementation techniques. 100%
Which of the following is TRUE regarding to IPSec? Takes place at the network layer
Which of the following is TRUE regarding to Secure Socket Layer (SSL)? Simple and well-
Which of the following is typically used to monitor the operation of network routers and switches? (d) Simple Network Management Protocol (SNMP) 100%
Which of the following is valid identifier? float int_2
Which of the following is(are) advantage(s) of the transistor over the vacuum tube? =All of the statements
Which of the following keyword is used to overload an operator? operator
Which of the following keywords is used to control access to a class member? Protected
Which of the following maps IP addresses onto datalink addresses? (d) Address Resolution Protocol (ARP) 100%
Which of the following methods can be used to isolate mobile code from the rest of the system? I.Monitoring system calls II.Running the code in a shared thread III.Interpreting the code execution (d) I and III only 100%
Which of the following network exploration tools can be used to determine information about possible paths between one network host and another? (d) Traceroute 100%
Which of the following output is correct about the program given below? } 200
Which of the following statement is correct about the program given below? The program will report compile time error.
Which of the following output is correct about the program given below? Protected
Which of the following output is correct about the program given below? Runtime error.
Which of the following protocols requires the transmission of a user's password or private key across the network? I.Kerberos II.Secure Socket Layer (SSL) (d) None 100%
Which of the following security threats is not typically addressed by encryption? (d) Denial of Service 100%
Which of the following SQL statements is correct? a. SELECT CustomerName, COUNT(customer_id) FROM Orders GROUP BY CustomerName?e. SELECT CustomerName, COUNT(*) FROM Orders GROUP BY CustomerName
Which of the following statement is correct about the program given below? The program will print the output 33.
Which of the following statement is correct about the program given below? The program will print the output 2 3 4.
Which of the following statement is correct about the program given below? The program will print the output Hi and Bye!.
Which of the following statement is correct about the program given below? The program will print the output 10 20.
Which of the following statement is correct about the references? A reference must always be initialized
Which of the following statement is correct?
Which of the following statement is correct? A function can be overloaded more than once.
Which of the following statement is correct? Destructor destroys the complete object.
Which of the following statement is correct? Overloaded functions can accept same number of arguments.
Which of the following statement is correct? The order of the default argument will be right to left.
Which of the following statement is correct? The order of the default argument will be right to left.
Which of the following statement is correct?A function can be overloaded more than once
Which of the following statement is NOT TRUE regarding key recovery via threshold schemes? If one trustee leaves the company, his or her share becomes invalid
Which of the following statement is NOT TRUE regarding key recovery via threshold schemes? A key is split into several shares, with all the shares must be combined to recover the secret
Which of the following statement is NOT TRUE? Any password the brute force attack tries, the dictionary attack also tries
Which of the following statement is NOT TRUE? A user must protect his/her public key
Which of the following statement is NOT TRUE? RSA encrypts at a speed on par with symmetric cryptosystems
Which of the following statement is NOT TRUE? The public key is kept secret while the private key may be widely distributed
Which of the following statement is TRUE? No one has been able to develop a public-key algorithm that has no weaknesses
Which of the following statement is TRUE? The password is mixed together with the salt
Which of the following statement is TRUE? There can be more than one public keys that correspond to a particular private key
Which of the following statements about computer viruses is false? Many viruses attach themselves to special parts on disks.
Which of the following statements about Java Database Connectivity (JDBC) is not true? (d) JDBC is an object-oriented implementation of ODBC. 100%
Which of the following statements are correct?
Which of the following statements are correct?1,2
Which of the following statements are correct about the below declarations2,3,4
Which of the following statements are correct about the program below? The code converts lower case character to upper case
Which of the following statements are TRUE regarding to Digital signature Digital signatures are used to authenticate the individual sending the message so as to ensure the integrity of the data.
Which of the following statements contains an error? b. SELECT stud_id WHERE stud_id = 45238 AND lastname = ‘Sabiev’;
Which of the following statements gets the total value of the column Salary in the Employees table? a. SELECT SUM(Salary) FROM Employees d. SELECT SUM(Salary) FROM Employees order by 1
Which of the following statements is (are) true of network protocols? (d) I only 100%
Which of the following statements is correct about the constructors and destructors? Constructors can take arguments but destructors cannot.
Which of the following statements is correct in C++? Structures can have functions as members
Which of the following statements is correct? Both data and functions can be either private or public.
Which of the following statements is TRUE? Digital signatures - content is digitally signed with an individual’s private key and is verified by the individual’s public key (definition)
Which of the following statements is TRUE? Odin iz nih budetPublic key is used to encrypt the KKDCPrivate key is used to encrypt the KKDCPublic key is used to encrypt the session key
Which of the following statements is TRUE? Public-key algorithms are slow compared to symmetric cryptography
Which of the following steps should you take when creating a DTD for an existing XML document? Please select all the correct answers. a. Noting which elements will contain text, and which will contain only other elements b. Determining whether certain elements' content must be present d. Deciding whether elements should appear in a specific order
Which of the following tags are valid? (check all valid options) b. <cell/> c. <cell />
Which of the following term is used for a function defined inside a class? Member function
Which of the following transport protocol functions is (are) typically implemented for audio streaming? I.End-to-end flow control II.Error control III.Congestion control(d) II only 100%
Which of the following types of events in a distributed system can typically be ordered arbitrarily? (d) Disjoint 100%
Which of the following types of traffic occur in intra-domain routing? (d) I, II, and III 100%
Which of the following was designed to solve the problem of IP address space fragmentation? (d) Classless Inter Domain Routing 100%
Which of the following ways are legal to access a class data member using this pointer? this->x
Which of the following will not protect you from spam? Popup blocker
Which of the followings are drawbacks of OTP?
Which of the statement is NOT TRUE regarding a program to break a cryptographic key? If the value is close to the key, the result will give some indication that it is close to the correct key.
Which of the statement is TRUE about stream ciphers? It generally far less code than block ciphers.
Which of the statement is TRUE? The larger the key size, the greater the range of possible values a key can be.
Which of the statement(s) below is (are) true regard to comments? I. Comments are needed to document program. II. Comments improve program readability
Which of the statement(s) below is (are) true regard to preprocessor directive? I. Begins with (#) hash sign. II. Processed before the program compiled. III. preprocessor directives (like #include) do not end with a semicolon.
Which of these are not valid path expressions of XPath? b. $
Which of these is a mixing algorithm? MD5
Which of these is a mixing algorithm? SHA1
Which of these is a problem if we share the key in advance to solve the key distribution problem?
Which of these is a stream cipher? RC4
Which of these is NOT a recommended guideline for a good password? Avoid using a character more than twice
Which of these is NOT a recommended guideline for a good password? Store
Which of these is NOT categorized block ciphers? RC4
Which of these is not considered a symmetric-key algorithm? RSA
Which of these is possibly the best password that user can choose? aLm4tyc?TY
Which of these is possibly the worst password that user can choose? 14G:c*%3wM*-l6g_Bnp?d86
Which of these statements is NOT TRUE? Without a key, if hackers are able to obtain the encrypted file, it is possible that they can obtain the program that converts it back.
Which of these statements is TRUE? In symmetric-key cryptography, the key that is used to encrypt data is the same key that is used to decrypt it.
Which of these types of cipher is most suitable to encrypt verbal communication via mobile phone? Stream
Which one of the following best describes the functionality of the address lines? =Are used to designate the source or destination of the data on the data bus.
Which one of the following best describes the functionality of the control lines? =Are used to control the access to and the use of the data and address lines.
Which one of the following best describes the functionality of the data lines? =Provide a path for moving data among system modules.
Which one of the following is the definition of Data Channel? =Data Channel is an independent I/O block, which is equipped with its own processor and own system of instructions. These instructions are stored in the main memory subsystem, but they are executed only by corresponding processor (of I/O block).
Which one of the following is the definition of Integrated circuit?=Integrated circuit is an electronic device made by printing thousands or even millions of tiny transistors and some other electronic elements on a small silicon crystal (chip), which are connected in a certain way and considered as entire one.
Which one of the following is the definition of Multiplexor? =Multiplexor is a device, which serves as a central commutator for data transfer among data channels, CPU and the main memory. It may be considered as a dispatcher (manager) of access to the main memory by CPU and data channels
Which one of the following is the definition of Program Flow Control? =Program Flow Control is an abstraction at the set of all possible sequences of execution in the program.
Which one of the following is the definition of the term Analog Computer? =A computing device, which processes data given in a form of continuously changing physical values, the meanings of which may be measured
Which one of the following is the definition of the term Computer System? =A device or a complex of devices, which is intended for mechanization or automating of data processing, and which is constructed on the base of electronic elements
Which one of the following is the definition of the term Configuration of Computer System? =A concrete composition of hardware devices and interconnections among them, which is used during a certain period of time.
Which one of the following is the definition of the term Data? =Base elements of information, such as numbers, letters, symbols and so on, which are processed or carried out by human or computer
Which one of the following is the definition of the term Digital Computer? =An electronic computing device, which receives a discrete input data, processes it in accordance with the list of instructions stored inside it and generates resulting output data
Which one of the following is the definition of the term Format? =A way of data representation, or a scheme of data positioning
Which one of the following is the definition of the term Information? =A matter conferred to the data
Which one of the following is the definition of the term Software? =A detailed instructions that control the operation of a computer system
Which one of the following is the definition of the term System? =A set of material or abstract objects, which are simultaneously considered as one whole (entire), and which have been united for achieving some certain results.
Which one of the following is the definition of Transistor? =Transistor is an electronic device on the base of semiconductor crystal, which has got three or more electrodes; it intended for amplification, generation or transformation electric oscillations.
Which one of the following options is correct? All of the statements
Which one of the following represents a correct order for b. INSERT, INTO, SELECT, FROM, WHERE
Which one of the following was the first successful commercial computer? =UNIVAC I
Which Operator is used in character comparisons with pattern matching? e. like
Which part of IAS performs the primary arithmetic and logical operations of the computer? =Arithmetic & Logic Circuits Unit
Which process divides the disk into sectors and tracks? =Formatting
Which register is responsible for serving for temporary storage operands and results in ALU in IAS? =Accumulator
Which register is responsible for serving for temporary storage operands and results in ALU in IAS? =Multiplier Quotient
Which register is responsible for serving for the temporary storage of the right instruction, which has been fetched in IAS? =Instruction Buffer Register
Which register is responsible for storing a word, which should be put into the memory or which just have been taken out of the memory in IAS? =Memory Buffer Register
Which register is responsible for storing address of the next word of instruction, which should be fetched next in IAS? =Program Counter
Which register is responsible for storing an address of the memory cell to which we call for write or read data in IAS? =Memory Address Register
Which register is responsible for storing an operation code of current instruction 8 bit width during process of its execution in IAS? =Instruction Register
Which register keeps track of the instructions in the program stored in memory? =Program counter
Which registers can interact with the secondary storage? =Memory address register (MAR)
Which scheme is required for performing the operation selection for the single-order ALU and 8-bit operation? =3-input decoder
Which software prevents Trojan horses from entering the system through back doors? Firewall
Which SQL statement is used to insert new data in a database? c. INSERT
Which statements enable programs to perform statements repeatedly as long as a condition remains true? Repetition statements
Which syntax of XML Namespaces is right? b. xmlns:f="http://www.w3schools.com/furniture"
Which three functional areas are provided by IPSec? Authentication, Confidentiality, and Key management
Which two of the following are correct when including “&” character within an element value? c. Use a CDATA section <Element1><![CDATA[you&me]]></Element1> d. Use the predefined entity reference “&аmр;” for the “&” character <Element1>you&me</Element1>
Which type of cipher maps a plaintext alphabet to a ciphertext alphabet, so that each letter of the plaintext alphabet maps to a single unique letter of the ciphertext alphabet.. monoalphabetic substitution cipher
Which type of cipher uses a separate monoalphabetic substitution cipher for each successive letter of plaintext, depending on a key. monoalphabetic substitution cipher
Which way of numbering in XSL is right? d. <xsl:number/>
Which XQuery's agregator computes the average? c. avg
Which XQuery's agregator computes the number of elements? a. count
Which XQuery's agregator computes the sum? b. sum
Which XQuery's agregator eliminates duplicates? a. distinct-values
While using the direct mapping technique, in a 24 bit system the higher order 5 bits is used for ________. =Tag
While using the direct mapping technique, in a 24 bit system the lower order 2 bits is used for ________. =Word
Why is it not desirable to reuse a stream cipher key? stream cipher is one that encrypts a digital data stream one bit or one byte at a time. A block cipher is one in which a block of plaintext is treated as awhole and used to produce a ciphertext block of equal length, // If two plaintexts are encrypted with the same key using a stream cipher, thencryptanalysis is often quite simple. If the two ciphertext streams are XORedtogether, the result is the XOR of the original plaintexts. If the plaintexts aretext strings, credit card numbers, or other byte streams with known properties,then cryptanalysis may be successful
Why is it not desirable to reuse a stream cipher key? If two plaintexts are encrypted with the same key using a stream cipher then cryptanalysis is often quite simple. If the two ciphertext streams are XORed together the result is the XOR of the original plaintexts. So it is not desirable to reuse a stream cipher key.
Why is it that the one-time pad can only be used once? If two messages encrypted with the same “one-time” pad key and when two different ciphertexts XORed with each other the key disappears
Why systems are vulnerable? Select right options b. Accessibility of networks c. Disasters d. Computers outside of firm control
Why Use a DTD? Select wrong sentence: b. With a DTD, we can keep information about foreign references to outside data files
With __________, the caller gives the called function the ability to access the caller's data directly and to modify it if the called function chooses to do so. passed by reference
With SQL, how can you delete the records where the "Price" is less than average price in the Purchase Table? d. DELETE FROM Purchase AS x WHERE x.Price < (SELECT AVG(x.Price) FROM Purchase AS x)
With SQL, how can you insert a new record into the "Students" table? d. INSERT INTO Students VALUES ('Jimmy', 'Jackson')
With SQL, how do you select a column named "Version" from a table named "Software" and a column named "Version" from a table named "Automobile"? e. SELECT Software.Version, Automobile.Version FROM Software,
With SQL, how do you select all the records from a table named "Persons" where the "LastName" is alphabetically between (and including) "Hansen" and "Pettersen"? c. SELECT LastName BETWEEN 'Hansen' AND 'Pettersen' FROM
With the addition of two machine numbers overflow the mantissa adder, which will require in this case, the normalization of the mantissa adder to the right level of 1 bit, the main discharge number mantissa adder will be in the junior secondary discharge. If it is "1" then the operation may be necessary to=rounding, adding 1 to the lowest category of the main mantissa adder
With the addition of two machine numbers, the sum of the mantissas may be greater than 1 (overflow the mantissa adder) to save this "1" is the highest extra bit mantissa adder. This situation requires=shift the mantissa adder, including her eldest extra bit for a bit to the right and a simultaneous increase in the order of 1 results
Write a query that will find all of the fields in the car table for those cars that were sold. Use a SUBQUERY with IN.Car(carid, name, model, year, maker) Carsale(carid, stickerprice, dealercost)
Write a query that will find all of the fields in the car table for those cars that were sold. Use EXISTS. Car(carid, name, model, year, maker) Carsale(carid, stickerprice, dealercost)
WSDL is used for describing the services available. a. True
XML publishing: XML --> relational data. Is it right? a. False
XML storage: XML --> relational data. Is it right? a. True
XML. An element declaration has the following syntax: b. <!ELEMENT element-name category>
XML. CDATA means: c. character data
XML. Elements with only character data are declared with d. #PCDATA
XML. PCDATA means: d. parsed character data
XPath expressivity sufficient... e. no simple navigation through the tree
XQuery. “Flower” Expressions are: a. LET b. RETURN c. WHERE e. FOR
XQuery. How many clauses in “Flower” Expressions?4
XQuery. Which order of clauses is right? e. FOR-LET-WHERE-RETURN
XSL. How do you divide 10 by 5? c. 10 div 5
XSL. How do you select all the og attributes in the document? e. //@og
XSL. How do you select the first two titles in the document: c. (//title)[position()<=2]
XSL. LET - Binds collection variables --> one value. Is it right? a. True
XSLT is a... a. high-level transformation language;
XSLT is: d. Extensible Stylesheet Language Transformation;
XSLT. Processing always starts at the root. Is it right? a. True
Zero defects cannot be achieved because complete testing is not possible with large programs a. True
Date: 2015-09-26; view: 765; Нарушение авторских прав