
Полезное:
Как сделать разговор полезным и приятным
Как сделать объемную звезду своими руками
Как сделать то, что делать не хочется?
Как сделать погремушку
Как сделать так чтобы женщины сами знакомились с вами
Как сделать идею коммерческой
Как сделать хорошую растяжку ног?
Как сделать наш разум здоровым?
Как сделать, чтобы люди обманывали меньше
Вопрос 4. Как сделать так, чтобы вас уважали и ценили?
Как сделать лучше себе и другим людям
Как сделать свидание интересным?

Категории:
АрхитектураАстрономияБиологияГеографияГеологияИнформатикаИскусствоИсторияКулинарияКультураМаркетингМатематикаМедицинаМенеджментОхрана трудаПравоПроизводствоПсихологияРелигияСоциологияСпортТехникаФизикаФилософияХимияЭкологияЭкономикаЭлектроника

The keystream should approximate the properties of a true random number stream as close as possible
|
|
The keyword ________ is used in a function header to indicate that a function does not return a value or to indicate that a function contains no parameters. void
The keyword _ const can be used to specify that an object is not modifiable and that any attempt to modify the object should result in a compilation error.
The keyword used to transfer control from a function back to the calling function is return
The left outer join is one type of outer join. Another one is the. d. all answers are right
The machine floating point number with base 2 ± 
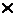
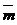 normalized (
normalized ( - n-rank mantissa, p - order) in case of: =a1=1
- n-rank mantissa, p - order) in case of: =a1=1
The machine number with base 2 ± 
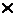
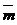 is normalized (
is normalized (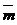 - mantissa, p - order) in case of:=1/2
- mantissa, p - order) in case of:=1/2 
 <1, 0
<1, 0 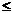 |p|
|p| 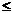 2k-1‚where k- the number of digits of the order
2k-1‚where k- the number of digits of the order
The main virtue for using single Bus structure is ___________.=Cost effective connectivity and ease of attaching peripheral devices
The memory blocks are mapped on to the cache with the help of ______. =Mapping functions
The memory devices which are similar to EEPROM but differ in the cost effectiveness is ______. =Flash memory
The method of mapping the consecutive memory blocks to consecutive cache blocks is called ______. =Direct
The multiplexor chip is a chip with n operating binary inputs and how many data inputs? =2n data inputs
The multiplexor chip is a chip with n operating binary inputs and how many outputs? =One output
The NOR gate is complement of which gate? =OR
The number failed attempts to access memory, stated in the form of fraction is called as _____________. =Miss rate
The number successful accesses to memory stated as a fraction is called as __________. =Hit rate
The number used to refer to a particular element of an array is called its _ subscript (or index)
The only integer that can be assigned directly to a pointer is 0_.
The operation of each individual component as part of the structure is known as _______________. =Function
The operator used for dereferencing or indirection is *
The original data, the input to an encryption function or the output of a decryption function. Plaintext
The output of an encryption algorithm; the encrypted form of a message or data. Ciphertext
The portion of a function prototype that includes the name of the function and the types of its arguments is called the function signature
The process of determining which competing bus master will be permitted access to the bus. =bus arbitration
The process of setting up routers to exchange connectivity information with each other is called (d) Peering 100%
The processing required for a single instruction is called a(n) _______________ =instruction cycle
The PROM is more effective than ROM chips in regard to which of the following=I and III
The reason for the implementation of the cache memory is =The difference in speeds of operation of the processor and memory
The registers, ALU and the interconnection between them are collectively called as _______________. =Data path
The result of dividing the 2-machine numbers (with n-bit mantissa) x '= ± 2p' • m2, x '= ± 2p'' • m2, if the dividend is greater than the divisor, then the result register =Loss of normalization occurs
The ROM chips are mainly used to store _______. =Boot files
The sign of the operation for the logical disjunction function has the form =V
The sign of the operation for the logical function of the conjunction of the form =&
The small extremely fast, RAM’s are called as ___________. =Cache
The strength of Diffie-Hellman public key scheme relies on the difficulty of: Discrete algorithm
The technology of video-signals recording and other data of a large volume is used and it’s based on methods of information (data) compression. =DVD
The term packetization refers to the process of (d) splitting a message into fragments for network transmission 100%
The throughput of a transmission medium is limited by which of the following factors? I.The width of the available frequency spectrum II.The effects of noise and attenuation III.The number of encoding levels in the signal (d) I, II, and III 100%
The time delay between two successive initiation of memory operation _____________. =Memory cycle time
The time that elapses between the initiation of an operation and completion of that operation is called _____________. =memory access time
The time that is taken for the sector to reach the head is known as _______________. =rotational latency
The time that is taken to position the head at the track is known as _____________. =seek time
The transfer's calculation optimization problem occurs during the addition of relatively long binary sets. The serial transfer gives the following rates: n/2 - average case, n - worst case. The question is: "How many operations are required to build a scheme with the worst case evaluation =const*〖log〗_2 n elementary operations
The translation of encrypted text or data into original text or data Decryption, Deciphering
The truth table for the construction of the complete conjunctive-normal form of the Boolean function should be fulfilled with the argument sets where the given function is equal to...?=Function is equal to 0
The truth table for the construction of the complete disjunctive-normal form of the Boolean function should be fulfilled with the argument sets where the given function is equal to...? =Function is equal to 1
The unit which decodes and translates each instruction and generates the necessary enable signals for ALU and other units is known as a (n) ______________.=control unit
The way in which the components are interrelated is known as _______________. =Structure
The Web services can not offer the application components like b. web browsers;
The word "asymmetric" in public-key cryptography means: The key to encrypt is different from the key to decrypt
There are three ways of applying an XSLT to an XML document. Which is NOT this way? c. Editing
There is a error in the below program. Which statement will you add to remove it? Add prototype: float func(int, float)
This markup language is considered to be extensible because of its unlimited and self-defining markup symbols. a. XML;
This XML extension is a standard way to describe how to transform the structure of an XML document into an XML document with a different structure. d. XSLT;
Time between presenting the address and getting the valid data (for random access) is known as a (n) _____________. =Access time
Time may be required for the memory to “recover” before next access is known as a (n) _____________. =Memory cycle time
TLS is: d. Transport Layer Security
To add an element to a vector for the first time, you normally use the member function push_back
To distinguish between two sectors in disks we make use of _____________. =Inter sector gap
To extend the connectivity of the processor bus we use ______.=PCI bus
To figure out the password by trying every possible keystroke combination is called: Brute force attack
To figure out the password by trying possible likely passwords froma list is called: Dictionary attack
Date: 2015-09-26; view: 362; Нарушение авторских прав