
Полезное:
Как сделать разговор полезным и приятным
Как сделать объемную звезду своими руками
Как сделать то, что делать не хочется?
Как сделать погремушку
Как сделать так чтобы женщины сами знакомились с вами
Как сделать идею коммерческой
Как сделать хорошую растяжку ног?
Как сделать наш разум здоровым?
Как сделать, чтобы люди обманывали меньше
Вопрос 4. Как сделать так, чтобы вас уважали и ценили?
Как сделать лучше себе и другим людям
Как сделать свидание интересным?

Категории:
АрхитектураАстрономияБиологияГеографияГеологияИнформатикаИскусствоИсторияКулинарияКультураМаркетингМатематикаМедицинаМенеджментОхрана трудаПравоПроизводствоПсихологияРелигияСоциологияСпортТехникаФизикаФилософияХимияЭкологияЭкономикаЭлектроника

II.Macro viruses infect documents, not executable portions of code
In ________ protocol the information is directly written into main memory. =Write through
In a distributed system, which of the following would best tolerate a Byzantine failure? (d) Mirroring with voting 100%
In a DTD, Attributes are declared with an _______ declaratio n. ATTLIST
In a remote procedure call (RPC) framework, the _____ is responsible for converting typed parameters into byte strings that can be transmitted over a network. (d) stub routine 100%
In addition to minuend, subtrahend's orders what does the difference result for the for the single-order adder-subtractor chip performing subtraction operation consider?=Lease value of the give order
In an integrated services model, which of the following is (are) necessary in order to provide network Quality of Service (QoS) guarantees? I.Admission control II.Traffic enforcement (d) I and II 100%
In an integrated services network, in order to offer Quality of Service (QoS), a packet classifier is required to (d) identify the type of the flow to which the packet belongs 100%
In an integrated services network, it is necessary to have a traffic enforcement mechanism to ensure that (d) applications do not exceed their agreed transmission rate 100%
In asymmetric key cryptography, the private key is kept by Receipient
In block ciphers, block size usually depends on the: Cryptosystem algorithm
In C++ Programming, how to represent a logical AND? &&
In C++, it is possible to have various functions with the same name that operate on different types or numbers of arguments. This is called function _ t types or numbers of arguments. This is called function overloading
In C++, the condition (4 > y > 1) Does not evaluate correctly and should be replaced by (4 > y && y > 1).
In CD-ROM which field contains the block address and the mode byte? =Header
In CD-ROM which field identifies the beginning of a block? =Sync
In cell-based wireless networks, the MAC protocol inside the cells is typically (d) broadcast-based 100%
In Centralised Arbitration which device(s) is/are is the bus master? =I and II
In Common Object Request Broker Architecture (CORBA), the static binding between a client and a remote object happens when the (d) source code is compiled 100%
In Common Object Request Broker Architecture (CORBA), which of the following is (are) true about the Interface Description Language (IDL)? (d) I, II, and III 100%
In cryptography, the order of the letters in a message is rearranged by Transposition
In cryptography, the original message before encryption is called: Plaintext
In Feistel Cipher an iterated cipher with an internal function called a ___________ function. Round
In Java Remote Method Invocation (RMI), a remote object registry is a _____ that _____ remote objects. (d) naming service, binds names with 100%
In Java Remote Method Invocation (RMI), which of the following is done by the RMI compiler? (d) Generating stubs and skeletons 100%
In magnetic disk data are transferred to and from the disk in ____________. =blocks
In magnetic disks data are stored in block-size regions known as _____________. =sectors
In multiplexer 8x1 what control bits we have to configure to get information from 1st pin =000
In multiplexer 8x1 what control bits we have to configure to get information from 2nd pin =001
In multiplexer 8x1 what control bits we have to configure to get information from 3rd pin =010
In multiplexer 8x1 what control bits we have to configure to get information from 4th pin =011
In multiplexer 8x1 what control bits we have to configure to get information from 5th pin =100
In multiplexer 8x1 what control bits we have to configure to get information from 6th pin =101
In multiplexer 8x1 what control bits we have to configure to get information from 7th pin =110
In multiplexer 8x1 what control bits we have to configure to get information from 8th pin =111
In network Quality of Service (QoS), which of the following does the traditional best-effort Internet service model guarantee? I.Packet delivery II.Latency limit III.Bandwidth (d) None 100%
In order to maintain network stability while Transmission Control Protocol (TCP) probes for additional bandwidth, rate increases are _____, and rate decreases are _____. (d) additive, multiplicative 100%
In order to obtain a reference in Java to a remote object in Remote Method Invocation (RMI), the URL passed to the naming service includes the _____ name and the host where the _____ is located. (d) object, registry 100%
In Quality of Service (QoS) networks, a fair queuing (FQ) scheduler typically consists of a _____ and a(n) _____. (d) packet classifier, actual scheduler 100%
In Quality of Service (QoS) networks, using a weighted fair queuing (WFQ) scheduler is a typical way to support (d) bandwidth reservation 100%
In RC4, the plaintext is broken into streams
In Remote Procedure Call (RPC) or Remote Method Invocation (RMI), a remote call will typically take _____ time and handle _____ exceptions than the equivalent local call. (d) greater, more 100%
In substitution cipher which of the following happens? Characters are replaced by other characters
In symmetric-key cryptography, symmetry means: The key that is used to encrypt data is the same key.
In synchronous bus, the devices get the timing signals from ~=A common clock line
In terms of code generation, how do the two definitions of buf, both presented above, differ? They do not differ - they are functionally equivalent.
In the "Key Distribution Center" scenario, the KDCs share and keep permanently with users their _____________. Master key
In the _______ statement, the loop-continuation condition test occurs at the beginning of the loop before the body of the loop executes. While (while do maybe)
In the following code, the p2 is Integer Pointer or Integer? Integer pointer
In the IETF Integrated Services (IntServ) model, which of the following is (are) available to an application that uses the guaranteed service class? I.A packet latency guarantee II.A bandwidth guarantee (d) I and II 100%
In Transmission Control Protocol (TCP), network traffic sources can dynamically increase transfer rate over time by (d) probing 100%
In video-streaming applications, per-frame compression exploits _____ redundancy in the data, whereas inter-frame compression exploits _____ redundancy in the data. (d) spatial, temporal 100%
In which access method access is accomplished by direct access to reach a general vicinity plus sequential searching, counting, or waiting to reach the final location? =Direct
In which access method any location can be selected at random and directly addressed and accessed? =Random
In which cache state he line in the cache does not contain valid data? =Invalid
In which cache state the line in the cache has been modified and it differs from that in the main memory, so it is available only in this cache? =Modified
In which cache state the line in the cache is the same as that in the main memory and also is not present in any other cache? =Exclusive
In which cache state the line in the cache is the same as that in the main memory and may be present in another cache? =Shared
In which of the following types of routing algorithms does every router maintain information about the complete network topology? (d) I only 100%
In which of the four basic password techniques a user is allowed to select his or her own password. At the time of selection, the system checks to see if the password is allowable and, if not, rejects it. Proactive
In which of the four basic password techniques the system periodically runs its own password cracker to find guessable passwords and cancels any passwords that are guessed and notifies the user. Reactive
In which of the four basic password techniques users can be told the importance of using hard-to-guess passwords and can be provided with guidelines for selecting strong passwords. User education
In Winchester Disk Track which component holds the control sum of the field? =CRC
In Winchester Disk Track which component identifies a head, since this disk has multiple surfaces? =Track number
In Winchester Disk Track which component is special bit pattern that determines the beginning of the field? =SYNCH byte
In Winchester Disk Track which component is unique identifier or address used to locate a particular sector? =ID field
Indicate functions of the computer system =All of the statements
Indicate important design considerations for a stream cipher. The encryption sequence should have a large period.
Indicate the definition for Access control. restricting
Indicate the definition for Anonymity. concealing
Indicate the definition for Authorisation. conveyance
Indicate the definition for Certification. endorsement
Indicate the definition for Confirmation. acknowledgement
Indicate the definition for Data integrity. ensuring
Indicate the definition for Entity authentication or identification. identifying
Indicate the definition for Message authentication. corroborating
Indicate the definition for Non-repudiation. Preventing
Indicate the definition for Ownership. providing
Indicate the definition for Privacy or confidentiality. Keeping
Indicate the definition for Receipt. Acknowledgement… received
Indicate the definition for Revocation. Retraction
Indicate the definition for Signature. binding
Indicate the definition for Timestamping. Recording the time
Indicate the definition for Validation. timliness
Indicate the definition for Witnessing. verifying
Indicate the drawbacks of reactive password checking technique. resource intensive any existing passwords remain vulnerable
Indicate the one of the purposes of salt used in the Unix password scheme. It prevents duplicate passwords
Indicate the one of the purposes of salt used in the Unix password scheme. It effectively increases
Indicate types of passive attack Release of message content Traffic analysis
Information Systems are a. Inventory System c. Payroll System
Information Tecnologies are a. Network System b. Software System c. Hardware System e. Database System
IS Development Challenges: a. Information c. Workforce downsizing
IS Development Opportunities: b. Enhanced global competitiveness c. Support corporate e. Capture market opportunities
IS Development. Choose the most right order of steps d. Investigation -> Analysis -> Design -> Implementation -> Maintenance&Review
Is the following DTD declaration valid?<!DOCTYPE personnel SYSTEM "./dtd/RplClient.dtd" --> False
Is the following text valid XML? <employee id="4" phone="00234567" phone="00434656">Teo Leo</employee> False
Is the following text valid XML? <employee id="4"> <name>Teo Leo</employee> </name> False
Is the following text valid XML? <employee id="4"> <phone>00234567</phone type="work"> <phone>00434656</phone type="home"> </employee> False
Is the following xml file well-formed?<!-- comment --><?xml version="1.0"?><root></root> False
Is the following XML valid? <AnElement some_attribute="<UpperCase>">Yes</AnElement> False
Is the follwing DTD definition valid?!ELEMENT RPLClient (TestSession)?> False
Is the follwing DTD definition valid?<! ELEMENT RPLClient (TestSession)?> False
Is the follwing DTD definition valid?<!ELEMENT RPLClient (TestSession)? True
It can convert your applications into Web-applications d. Web Services;
It is known that to achieve the logical function "disjunction" is required =Three transistors
It is known that to achieve the logical function "negation of the conjunction" (NAND) is required =Two transistors
It is known that to achieve the logical function "negation of the disjunction" (NOR) is required =Two transistors
Keyword_ s truct _introduces a structure declaration.
Keywords public, private and protected are _ access specifiers
Let 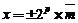 be a floating point number with the base 2 and let n be the size of mantissa and k the total amount of cells. What is the minimum normalized number that is not equals to zero?=
be a floating point number with the base 2 and let n be the size of mantissa and k the total amount of cells. What is the minimum normalized number that is not equals to zero?= 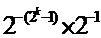
Let 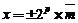 be a floating point number with the base 2 and let n be the size of mantissa and k the total amount of cells. What is the minimum NOT normalized number that is not equals to zero?=
be a floating point number with the base 2 and let n be the size of mantissa and k the total amount of cells. What is the minimum NOT normalized number that is not equals to zero?= 
Let  be a floating point number and let n be the size of mantissa and k the size of the cells. What is the minimum normalized number that is not equals to zero such as
be a floating point number and let n be the size of mantissa and k the size of the cells. What is the minimum normalized number that is not equals to zero such as  =
= 
Let ± 
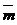 be a machine number with k cell size n mantissa. What is the maximum number that can be represented?=
be a machine number with k cell size n mantissa. What is the maximum number that can be represented?= 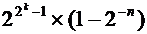
Let m=10, n=3, where n size of mantissa. For the number x that is equal to 0,317 with good precision result number can be=100 * 0, 3171
Let the base of the system be m \= 8.Let we have n length cell. We are putting dot on the right of the LSB(Least Significant Bit) cell and checking number with fixed point. MSB (Most Significant Bit) will be responsible for the minus or plus sign. What is the maximum number that can be stored in given cell?  =If we will write αi=7, where i=1,2,...,n in all remained positions
=If we will write αi=7, where i=1,2,...,n in all remained positions
Let the base of the system be m = 2.Let we have n length cell. We are putting dot on the right of the LSB(Least Significant Bit) cell and checking number with fixed point. MSB (Most Significant Bit) will be responsible for the minus or plus sign. What is the maximum number that can be stored in given cell?  =If we will write αi=1, where i=1,2,...,n in all remained positions
=If we will write αi=1, where i=1,2,...,n in all remained positions
Let the base of the system be m = 2.Let we have n length cell. We are putting dot on the right of the LSB(Least Significant Bit) cell and checking number with fixed point. MSB (Most Significant Bit) will be responsible for the minus or plus sign. What is the maximum number that can be stored in given cell?  ~ =2n-1
~ =2n-1
Let the base of the system be m = 4.Let we have n length cell. We are putting dot on the right of the LSB(Least Significant Bit) cell and checking number with fixed point. MSB (Most Significant Bit) will be responsible for the minus or plus sign. What is the maximum number that can be stored in given cell?  =If we will write αi=3, where i=1,2,...,n in all remained positions
=If we will write αi=3, where i=1,2,...,n in all remained positions
Let the floating-point number is х= ±mp 
 , where m is the base, p-order of ̅m - and an n-bit mantissa. We normalized the number of x =a1!\= 0(a1 is first bit of mantissa)
, where m is the base, p-order of ̅m - and an n-bit mantissa. We normalized the number of x =a1!\= 0(a1 is first bit of mantissa)
Let the integer m be the base of the system, where m \= 2. What most significant digit that can be used in m based system?{ =1
Let the integer m be the base of the system, where m \= 4. How many significant digits can be used to record one position in a number with such base?{ =4
Let the integer m be the base of the system, where m \= 4. What most significant digit that can be used in m based system?{ =3
Let the integer m be the base of the system, where m \= 4. What symbols are used to denote m based numbers? =0,1,2,3
Let the integer m be the base of the system, where m \= 8. How many significant digits can be used to record one position in a number with such base?{ =8
Let the integer m be the base of the system, where m \= 8. What most significant digit that can be used in m based system? =7
Let the integer m be the base of the system, where m \= 8. What symbols are used to denote m based numbers? =0,1,2,3..7
Let the integer m be the base of the system, where m = 10. What most significant digit that can be used in m based system? =9
Let the integer m be the base of the system, where m = 16. How many significant digits can be used to record one position in a number with such base? =16
Let the integer m be the base of the system, where m = 16. What most significant digit that can be used in m based system? =F
Let the integer m be the base of the system, where m = 16. What symbols are used to denote m based numbers? =0,1,2,3..9,A,B,C,D,E,F
Let the integer m be the base of the system, where m = 2. How many significant digits can be used to record one position in a number with such base? =2
Let the integer m be the base of the system, where m = 2. What symbols are used to denote m based numbers? =0,1
Location in memory where value can be stored? Variable or scalar (ne tochno)
Malicious hacker tools used to break into new machines remotely is known as a(n) _____________. Auto-rooter
Management Support System are b. Decision support systems c. Executive information systems
Mechanism by which other modules (e.g. I/O, memory) may interrupt normal sequence of processing is known as _______________. =interrupt
Member function size of class template vector returns the number of elements in the vector on which it is invoked.
Memory in which each addressable location has a unique addressing mechanism. The time to access a given location is independent of the sequence of prior access. =RAM
Memory unit that communicates directly with the CPU is called the ______________. =Main memory
Memory-resident virus: Lodges in main memory as part of a resident system program. From that point on, the virus infects every program that executes.
Metal or plastic disk coated with magnetizable material is known as a(n) _________________. =Magnetic Disk
Metamorphic virus: A virus mutates with every infection. These virus r ewrites itself completely at each iteration, increasing the difficulty of detection. Metamorphic viruses my change their behavior as well as their appearance.
Most symmetric block encryption algorithms in current use are based on which cipher structure?This structure reveals the principles behind these more recent ciphers. Feistal
Multicast communication generally refers to data that is (d) sent from one host to several hosts simultaneously 100%
Network clients use well-known _____ numbers to contact well-defined network services, such as Telnet and DNS servers. (d) port 100%
No central controller. Instead each module has access control logic and the modules act together to share the bus. =Distributed
Numbers and encoded characters generally used as operands is known as a(n) ____________. =Data
Observing pattern of the message is known as ___________ Traffic analysis
On a network, the term authentication typically refers to the process of (d) verifying the identity of a sender or receiver 100%
One of the best known and most widely implemented trusted third party key distribution systems is known as _____________. Kerberous
One type of an optical disk that is more easily written than CD-ROM, making single-copy disks commercially feasible; holds from 200 to 800 Mbytes of data. =WORM
Operation which maps elements of the plaintext into another is known as ___________. Substitution
Operation which rearranges elements of the plaintext is known as ___________. Transposition
Operations Support Systems are b. Process control systems c. Office automation systems d. Transaction processing systems
Optical multi-level storage implemented for video with very high capacity? =DVD
Optical storage originally implemented for audio where data is stored as pits and data is read by reflecting laser? =CD-ROM
Parasitic virus: The traditional and still most common form of virus. This virus attaches itself to executable files and replicates, when the infected program is executed, by finding other executable files to infect.
People who use USE CASE diagrams: a. Customers b. Testers c. Use-case
Placing a new value into a memory location is said to be destructive
Please select right way of applying an XSLT to an XML document b.
Point out the error in the following program display() is called before it is defined
Point out the error in the program Redeclaration of a
Point out two major advantages of public crypto over symetric key crypto. With public key crypto, we don’t need to established a shared key in advance; Digital signatures offer not only integrity but also non-repudiation
Polymorphic virus: A virus that mutates with every infection, making detection by the "signature" of the virus impossible.
Private key is used to encrypt the session keyPublic key is used to encrypt the password
Program Counter (PC) is also called ______________. =Instruction pointer
PROM stands for =Programmable Read Only Memory.
Propagation phase: The virus places an identical copy of itself into other programs or into certain system areas on the disk. Each infected program will now contain a clone of the virus, which will itself enter a propagation phase.
Public-key cryptography is important because it solves: The key distribution problem
Rate at which data can be transferred into or out of a memory unit. is known as a (n) _____________. =Transfer rate
Reading variables from memory is known as nondestructive
Referring to the sample code below, what value will the variable counter have when completed? 2
Return type void indicates that a function will perform a task but will not return any information when it completes its task.
Secret entry point into program that allows entry without going through normal security access procedures is known as a(n) _______________. Trapdoor
Select one of the advantages of representing integers as the code with offset. =absence of dual representation of a "zero"
Select which of the following is a correct element type declaration for the occurrence of the “FirstName” element and the “LastName” element in that order as the child element of “Name” Element. a. <!ELEMENT Name (FirstName, LastName)>
Select which of the following is a correct XML declaration description. b. <?xml version="1.0"?>
Select which of the following is the specification used when transforming XML documents to HTML. c. XSLT
Select which of the following XML documents are well-formed XML documents. a. <productname>Dehumidifier "XZ001" </productname>
Select which two of the following are described as the top-level element in an XSLT stylesheet. The XSLT namespace prefix is “xsl”. b. xsl:template d. xsl:output
Self contained malicious programs that can be scheduled and run by the O/S is known as a(n) _______________. Host independent
Semiconductor memory whose contents cannot be altered, except by destroying the storage unit. Nonerasable memory. =ROM
Set of hacker tools used after attacker has broken into a computer system and gained root-level access is known as a(n) _______________. Rootkit
Set of rules and procedures developed by management in conjunction with security professionals is known as a(n) ___________________. Security policy
Set of tools for generating new viruses automatically is known as a(n) _____________. Kit(virus generator)
SOAP is used to transfer the: d. data
Socket-level programming typically involves (d) explicit send and receive calls to exchange data 100%
Software that controls the execution of programs and that provides services such as resource allocation, scheduling, input/output control, and data management. =Operating system
Software that is intentionally included or inserted in a system for a harmful purpose is known as a ________________. Malicious software
Some distributed file systems allow multiple copies of files due to caching. Which of the following types of distributed file servers leave(s) the resolution of file consistency issues up to the users? I.Stateless II.Stateful (d) I only 100%
Sometimes the expression "select count(*)" will return fewer rows than the expression "select count(value)". False
SSL is: d. Secure Sockets Layer
State whether the following statement is True or False for cache memory.=True, True, False
State whether the following statement is true. I. A macro virus is platform independent.
State whether true of false. I. A worm mails a copy of itself to other systems. II. A worm executes a copy of itself on another system.
Stealth virus: A form of virus explicitly designed to hide itself from detection by antivirus software.
Storage used to compensate for a difference in rate of flow of data, or time of occurrence of events, when transferring data from one device to another is known as _______________. =Buffer
string *x, y;
Suppose a and b are integer variables and we form the sum a + b. Now suppose c and d are floating-point variables and we form the sum c + d. The two + operators here are clearly being used for different purposes. This is an example of operating overloading
Suppose that your plaintext is 112 bytes long and you are using DES, how many bytes are needed for padding? 0
Suppose that your plaintext is 115 bytes long and you are using RC4, how many bytes are needed for padding? RC4 does not need padding
Suppose that your plaintext is 130 bytes long and you are using DES, how many blocks will be formed for the whole encryption process? 17
Suppose that your plaintext is 130 bytes long and you are using DES, how many blocks will be formed for the whole encryption process? 17
Suppose that your plaintext is 168 bytes long and you are using DES, how many blocks will be formed for the whole encryption process? 21
Suppose that your plaintext is 228 bytes long and you are using RC4, how many bytes are needed for padding? RC4 does not need padding
Suppose that your plaintext is 92 bytes long and you are using RC4, how many blocks will be formed for the whole encryption process? 0
System Vulnerability and Abuse. "Evil twins" is a. Wireless networks that pretend to offer trustworthy Wi-Fi connections to the Internet
System Vulnerability and Abuse. Click fraud is e. Occurs when individual or computer program dishonestly presses on online ad without any intention of learning more about the advertiser or making a purchase
System Vulnerability and Abuse. Identity theft is e. Steal of personal Information (social security id, driver
System Vulnerability and Abuse. Key logger is a. Record every keystroke on computer to steal serial numbers, passwords, launch Internet attacks
System Vulnerability and Abuse. Pharming is e. Redirects users to a bogus Web page, even when individual types correct Web page address into his or her browser
System Vulnerability and Abuse. Phishing is b. Setting up fake Web sites or sending e-mail messages that look like legitimate businesses to ask users for confidential personal data
System Vulnerability and Abuse. Phishing is a. Email designed to fool recipients into divulging personal information
System Vulnerability and Abuse. Spoofing is e. Misrepresenting oneself by using fake e-mail addresses or masquerading as someone else
System Vulnerability and Abuse. Spyware is b. Small programs install themselves surreptitiously on computers to monitor user Web surfing activity and serve up advertising
System Vulnerability and Abuse. SQL injection is b. Hackers submit data to Web forms that exploits site
System Vulnerability and Abuse. Trojan is e. Software program that appears to be benign but then does something other than
System Vulnerability and Abuse. Virus is d. Rogue software program that attaches itself to other software programs or data files in order to be executed
System Vulnerability and Abuse. Worm is b. Independent computer programs that copy themselves from one computer to other computers over a network
Take into account the fact that some Playfair keys produce the same encryption results. How many effectively unique keys does the Playfair cipher have? 24
That portion of the instruction cycle during which the CPU checks for interrupts. If an enabled interrupt is pending, the CPU saves the current program state and resumes processing at an interrupt-handler routine. =Interrupt cycle
That portion of the instruction cycle during which the CPU fetches from memory the instruction to be executed. =Fetch cycle
That portion of the instruction cycle during which the CPU performs the operation specified by the instruction opcode. Execute cycle
The __ Linear search compares each element of an array with a search key.
The ________ enables access to a global variable with the same name as a variable in the current scope. ::
The ________ method provides a one-time session key for two parties. Diffie-Hellman
The _________ attack can endanger the security of the Diffie-Hellman method if two parties are not authenticated to each other. Man-in-the-middle
The ________ statement in a called function passes the value of an expression back to the calling function. return
The __________________ is a group of bits that instruct the computer to perform a specific operation. It is usually divided into parts, each having its own particular interpretation. =instruction code
The __ delete_ operator reclaims memory previously allocated by new.
The __ do while _____ statement tests the loop-continuation condition after the loop body executes; therefore, the loop body always executes at least once.
The “natural” unit of organization of memory is known as a (n) _________. =Word
The algorithm developed by Feistel at IBM in the early 1970s and later adopted as a U.S. Federal Information Processing Standard for encrypting unclassified information is known as Data Encryption Standard
The algorithm that replaces block in the set that has been in the cache longest is known as ___________. =First in first out (FIFO)
The algorithm that replaces block in the set that has been in the cache longest with no reference to it is known as ___________. =Least Recently used (LRU)
The algorithm that replaces block in the set that has experienced the fewest references is known as ___________. =Least frequently used (LFU)
The algorithm to remove and place new contents into the cache is called _______. =Replacement algorithm
The amount of summands in the expansion formula ⋁& according to the given function's truth table during the construction of the complete conjunctive-normal form of the given Boolean function is equal to...? =Number of argument sets where the function is undefined
The amount of summands in the expansion formula ⋁& according to the given function's truth table during the construction of the complete disjunctive-normal form of the given Boolean function is equal to...? =Number of ones (1) n the truth table values' column
The classification of buses into synchronous and asynchronous is based on =The Timing of data transfers
The cons t qualifier is used to declare read-only variables.
The contents of the EPROM are earsed by =Exposing the chip to UV rays.
The control unit controls other units by generating __________. =Timing signals
The conversion of plaintext or data into unintelligible form by means of a reversible translation, based on a translation table or algorithm. Encryption, enciphering
The correspondence between the main memory blocks and those in the cache is given by _________. =Mapping function
The definition of a above explicitly initializes its first four elements. Which one of the following describes how the compiler treats the remaining four elements? The remaining elements are initialized to zero(0)
The delays caused in the switching of the timing signals is due to =Propagation delay
The device which starts data transfer is called __________. =Initiator
The disk system consists of which of the following: =I,II and III
The Distributed Computing Environment (DCE) supports which, if any, of the following? (d) None 100%
The drawback of building a large memory with DRAM is =The slow speed of operation.
The effectiveness of the cache memory is based on the property of ________. =Locality of reference
The elements of an array are related by the fact that they have the same _____ and _______. name, type
The first major change in the electronic computer came with the replacement of the vacuum tube by the _____________ =transistor
The following property is NOT used for the user authentication: Something that you individually share
The following protocols and system are commonly used to provide various degrees of security services in computer network. I. IP filtering III. IP security Architecture (IPsec) IV. Firewall
The Internet Protocol (IP) defines the _____ layer of the Internet protocol stack. (d) network 100%
Date: 2015-09-26; view: 392; Нарушение авторских прав; Помощь в написании работы --> СЮДА... |